
Social media has become an integral part of our daily routine, as social media platforms are now used as a place to gather news, connect and share images, posts, or videos with others. However social engineering attacks have made people cautious and the need for understanding and safeguarding from social hacking is an essential one.
The threat of social hacking is quite an old one but the recent case of 500 million Facebook users has left people not being able to trust anyone. The personal information of 500 million Facebook users was posted on a low-profile hacking forum. This data consisted of full names, phone numbers, emails, addresses, and other biographical information.
The personal information of many Facebook users can be used by criminals for ID theft and committing other frauds. Before we dive deep into solving the issue of social hacking, it would be best to understand what social hacking is.
What is Social Hacking?
Social hacking or social engineering hacking is not the traditional cyber-crime approach for hackers, as instead of using weaknesses in technology to attack and gain information, they target human weaknesses. It is a way of tricking people into enabling access to information or divulging data.
Most of the social engineering attacks take place when intruders pose as IT help desk representatives and request information such as usernames and passwords. It’s surprising how many people give away this personal information without even thinking twice. These social hackers use deception to manipulate and gather information from individuals.
Types of Social Engineering Attacks:
There are several types of attacks that social engineers can attempt and it’s essential to understand all of these types so that you can identify if you are being part of one. Here are a few types of social hacking attacks that commonly take place.
- Baiting:
Baiting is one of the oldest tricks in the book, as it involves social hackers setting up a trap that could be as simple as a malware-loaded USB. Waiting for someone to pick it and be curious enough to see what’s in the drive-by connecting it to their PC. This often results in the PC being compromised and information being corrupted.
- Pre-Texting:
This is a social hacking technique that involves gaining the attention of individuals by texting them and tricking them into providing personal information. It usually starts as an innocent internet survey and can end up in collecting your bank details.
- Phishing:
Phishing is a type of social hacking attack that targets individuals via text or emails from reputable service providers requesting confidential information. It can be a bank asking all their customers to verify their bank information, which is then redirected to a fake site that records all credential information. Most bank frauds are committed using this technique and hackers can also request confidential data for the organization from executives posing as their superior executives,
Ways to Avoid Social Engineering Attacks:
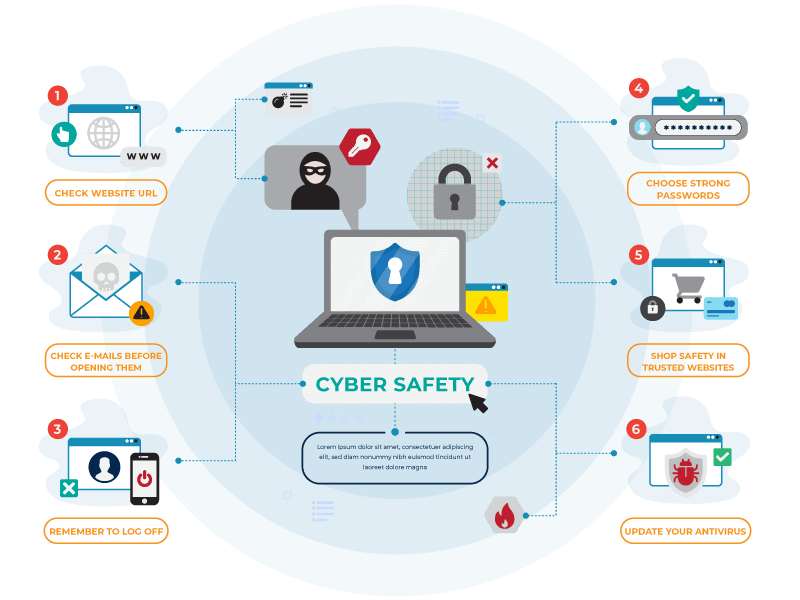
Avoiding social engineering attacks can be quite difficult at times, as they target the natural characteristics of human beings such as curiosity, trust, and respect. However, some ways can help you identify these frauds and save yourself from harm. Here are some of the effective ways to help you avoid social hacking attacks.
- Verify the Source:
It’s important to identify the source of anything suspicious instead of trusting it immediately. No matter if it’s an email from your boss requesting information regarding other employees, a message informing you that you have won a reward of $1 million, or a USB stick lying on your desk and not knowing from whom it is are all signs that require a fact check.
It’s not such a difficult task to verify the source, as you can easily go to the bank’s official site to get in touch with their customer support about the issue. As far as the email from a boss is concerned, you can compare it with an old authentic email to the one you’ve got and check spoofed hyperlinks.
- Find Out What They Know:
It’s best to know what others know before you provide them with all your details. In the case of a bank asking for information, they would surely have most of your information beforehand. Therefore, it would be best to confirm your details first from others rather than giving it all out voluntarily.
- Double Check:
Social hackers often depend on the sense of emergency and use this method to get you off your game, so that you are unable to assess the situation. This sense of emergency can lead to making rash decisions. Therefore, the best approach is to take a moment to think and use another communication method to double-check.
If a friend emails you to wire money immediately, the best course of action would be to call them on the phone or text them. This would verify all doubts that you might be being scammed.
Conclusive Thoughts:
People have lo been the victims at the hands of social hackers, as they use human characteristics to get confidential information or access that information. That gathered information is used for ID frauds, scams, and other criminal activities. It’s always important to understand and safeguard yourself from such attacks and the ways mentioned above can help you avoid these social hacking attacks.
Investing in cyber-security is no longer insurance against hackers, as social hacking poses an even greater risk to individuals. It is a misrepresentation of all moral and ethical boundaries and should be avoided at all costs.

